VEH hooking is a method of hooking into your target program without having to modify any of its bytes, thus bypassing CRC checks. It's slow and cannot be used for hooks that would be called often, though it is extremely stealthy. It works by causing an exception at the desired soon-to-be-hooked address, and creating a hook within the exception handler. We cause the exception by changing the memory protection of the memory page where our desired hook address is located. (PAGE_GUARD & PAGE_NOACCESS are two memory protections that will cause an exception to be thrown whenever any of the code within the page is executed.) And the exception handler that we create, which is outside of our target program's code, catches the exception and checks to see if the address that's currently being executed is the one we want to hook. If it is, we change the EIP (instruction pointer) to point to our function instead. When our function is done, we JMP back to wherever we need to be.
Here's an example of an allocated memory page. Let's say we want to create our hook at 0x08048fb7.
![]()
With VirtualProtect() we can change that memory page's protection to include PAGE_GUARD, which will cause the exception STATUS_GUARD_PAGE_VIOLATION to be thrown whenever any of its memory is executed.
However, as you can tell from MSDN, once the exception is thrown "the system also clears the PAGE_GUARD modifier, removing the memory page's guard page status." So we'll be constantly re-applying the PAGE_GUARD modifier in order to keep getting exceptions all throughout the page, to get to the address we're specifically after.
Credits to Ch40zz from rohitlab. (I modified it as I saw needed.)
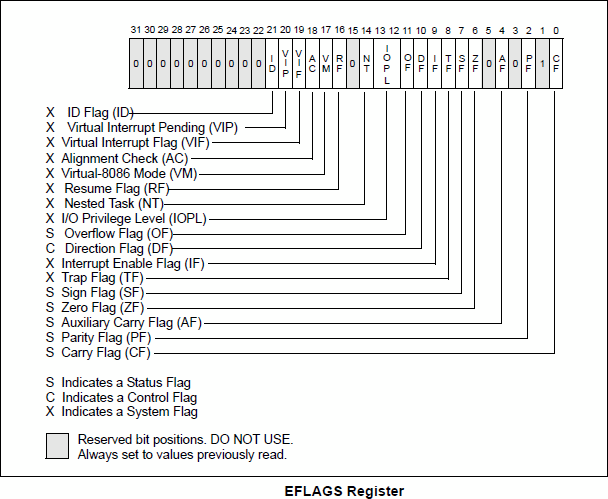
Here's a visual of the EFlags register:
![]()
As you can see, the 8th bit activates the Trap Flag (Single-step interrupt).
0x100 to binary is 000100000000. The bitwise OR operator |: simply turns it on.
For more information on using PAGE_NOACCESS to accomplish the same thing, check out DarkstaR's blogpost and example code.
This can be used to hack any game
Originally posted @ http://guidedhacking.com/showthread....-In-depth-Look
Here's an example of an allocated memory page. Let's say we want to create our hook at 0x08048fb7.

With VirtualProtect() we can change that memory page's protection to include PAGE_GUARD, which will cause the exception STATUS_GUARD_PAGE_VIOLATION to be thrown whenever any of its memory is executed.
However, as you can tell from MSDN, once the exception is thrown "the system also clears the PAGE_GUARD modifier, removing the memory page's guard page status." So we'll be constantly re-applying the PAGE_GUARD modifier in order to keep getting exceptions all throughout the page, to get to the address we're specifically after.
Credits to Ch40zz from rohitlab. (I modified it as I saw needed.)
Code:
DWORD dwOld;
VirtualProtect((void*)0x08048fb7, 1, PAGE_EXECUTE | PAGE_GUARD, &dwOld); // This sets the protection for whatever memory page that 0x08048fb7 is located in to PAGE_EXECUTE & PAGE_GUARD.
// Which is going to cause an exception for any address accessed in that memory page, including the one we're after.
AddVectoredExceptionHandler(true, (PVECTORED_EXCEPTION_HANDLER)UnhandledExceptionFilter); // Registers our vectored exception handler which is going to catch the exceptions thrown.
unsigned long UnhandledExceptionFilter(EXCEPTION_POINTERS *pExceptionInfo)
{
if (pExceptionInfo->ExceptionRecord->ExceptionCode == STATUS_GUARD_PAGE_VIOLATION) // This is going to return true whenever any of our PAGE_GUARD'ed memory page is accessed.
{
if (pExceptionInfo->ContextRecord->Eip == 0x08048fb7) // Here we check to see if the instruction pointer is at the place where we want to hook.
{
dwJmpBack = (DWORD*)(pExceptionInfo->ContextRecord->Esp + 0); // Find the return address for the JMP/EIP back into the target program's code.
dwJmpBack = (DWORD)pExceptionInfo->ContextRecord->Eip + 5; // or just skip X number of bytes.
pExceptionInfo->ContextRecord->Eip = (DWORD)hkFunction; // Point EIP to hook handle.
}
pExceptionInfo->ContextRecord->EFlags |= 0x100; //Set single step flag, causing only one line of code to be executed and then throwing the STATUS_SINGLE_STEP exception.
return EXCEPTION_CONTINUE_EXECUTION; // When we return to the page, it will no longer be PAGE_GUARD'ed, so we rely on single stepping to re-apply it. (If we re-applied it here, we'd never move forward.)
}
if (pExceptionInfo->ExceptionRecord->ExceptionCode == STATUS_SINGLE_STEP) // This is now going to return true on the next line of execution within our page, where we re-apply PAGE_GUARD and repeat.
{
DWORD dwOld;
VirtualProtect((void*)0x08048fb7, 1, PAGE_EXECUTE | PAGE_GUARD, &dwOld);
return EXCEPTION_CONTINUE_EXECUTION;
}
return EXCEPTION_CONTINUE_SEARCH;
}
As you can see, the 8th bit activates the Trap Flag (Single-step interrupt).
0x100 to binary is 000100000000. The bitwise OR operator |: simply turns it on.
For more information on using PAGE_NOACCESS to accomplish the same thing, check out DarkstaR's blogpost and example code.
This can be used to hack any game
Originally posted @ http://guidedhacking.com/showthread....-In-depth-Look